MAAD-AF Disable Tenant MFA¶
This module allows an attacker to disable any tenant level MFA policy enabled for an Azure AD user. Adversaries can use this as technique to disable defenses in order to launch further attacks on the account.
Module Overview - DRAFT¶
NOTE TO ENABLEMENT TEAM: We may need to find a more sustainable example to use for lab users and adjust the verbiage below accordingly.
From the main Attack Arsenal menu, enter
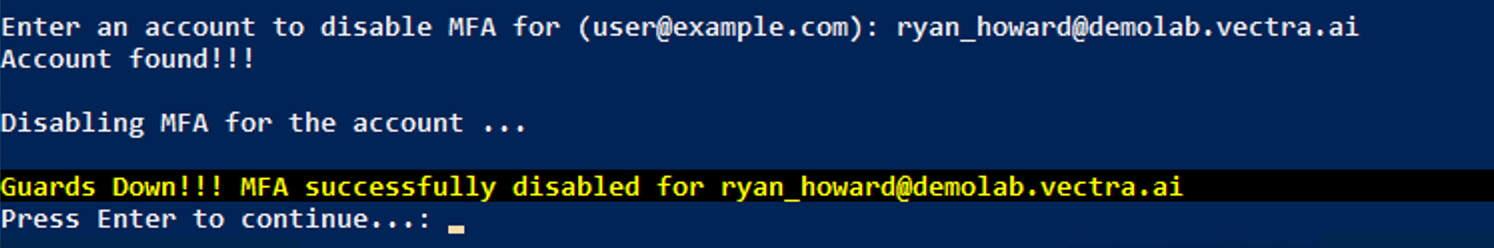
12forDisable Tenant Level MFA Policies for Easier Access. Read through the MITRE information, and press<Enter>to continue.Launch a Brute Force attack against the
ryan_howard@demolab.vectra.aiaccount. Enter this address when prompted.Note that simply pressing
<Enter>here will list all of the active accounts in the Azure AD tenant, in the event the attacker doesn’t doesn’t have a specific address already in mind to target.If the tenant MFA policy was successfully disabled for the specified user, MAAD-AF will display details of its findings. The module will print a failure or success message, as seen below: